Недавно я добавил NAT правила в моей системе RHEL 6.x. Как просмотреть правило, включая номер строки, которое я только что добавил?nnВы можете легко просматривать ваши правила, используя следующие команды на Linux:n
iptables command - IPv4 netfilter admin tool.nip6tables command - IPv6 netfilter admin tool.
Просмотр всех Iptables правила в Linux
Синтаксис команды следующийn
iptables --listniptables -Lniptables --table NameHere --listniptables -t NameHere -L -n -v --line-numbers
Например, выполните следующую команду под root пользователемn
# iptables -L
Результатn
Chain INPUT (policy DROP)ntarget prot opt source destinationnACCEPT tcp -- google-public-dns-a.google.com anywhere tcp dpt:domainnACCEPT udp -- google-public-dns-a.google.com anywhere udp dpt:domainnACCEPT tcp -- google-public-dns-a.google.com anywhere tcp spt:domainnACCEPT udp -- google-public-dns-a.google.com anywhere udp spt:domainnLOCALINPUT all -- anywhere anywherenACCEPT all -- anywhere anywherenINVALID tcp -- anywhere anywherenACCEPT all -- anywhere anywhere state RELATED,ESTABLISHEDnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ftp-datanACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ftpnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:sshnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:smtpnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:domainnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:httpnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:pop3nACCEPT tcp -- anywhere anywhere state NEW tcp dpt:imapnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:httpsnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:urdnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:submissionnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:imapsnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:pop3snACCEPT tcp -- anywhere anywhere state NEW tcp dpt:cdcnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:atmtcpnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:mysqlnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:5666nACCEPT tcp -- anywhere anywhere state NEW tcp dpts:50000:51000nACCEPT udp -- anywhere anywhere state NEW udp dpt:ftp-datanACCEPT udp -- anywhere anywhere state NEW udp dpt:ftpnACCEPT udp -- anywhere anywhere state NEW udp dpt:domainnACCEPT icmp -- anywhere anywhere icmp echo-request limit: avg 1/sec burst 5nACCEPT icmp -- anywhere anywhere icmp echo-reply limit: avg 1/sec burst 5nACCEPT icmp -- anywhere anywhere icmp time-exceedednACCEPT icmp -- anywhere anywhere icmp destination-unreachablenLOGDROPIN all -- anywhere anywherennChain FORWARD (policy DROP)ntarget prot opt source destinationnnChain OUTPUT (policy DROP)ntarget prot opt source destinationnACCEPT tcp -- anywhere google-public-dns-a.google.com tcp dpt:domainnACCEPT udp -- anywhere google-public-dns-a.google.com udp dpt:domainnACCEPT tcp -- anywhere google-public-dns-a.google.com tcp spt:domainnACCEPT udp -- anywhere google-public-dns-a.google.com udp spt:domainnLOCALOUTPUT all -- anywhere anywherenACCEPT tcp -- anywhere anywhere tcp dpt:domainnACCEPT udp -- anywhere anywhere udp dpt:domainnACCEPT tcp -- anywhere anywhere tcp spt:domainnACCEPT udp -- anywhere anywhere udp spt:domainnACCEPT all -- anywhere anywherenINVALID tcp -- anywhere anywherenACCEPT all -- anywhere anywhere state RELATED,ESTABLISHEDnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ftp-datanACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ftpnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:sshnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:smtpnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:domainnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:httpnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:pop3nACCEPT tcp -- anywhere anywhere state NEW tcp dpt:authnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:httpsnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:submissionnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:imapsnACCEPT tcp -- anywhere anywhere state NEW tcp dpt:pop3snACCEPT tcp -- anywhere anywhere state NEW tcp dpt:atmtcpnACCEPT udp -- anywhere anywhere state NEW udp dpt:ftp-datanACCEPT udp -- anywhere anywhere state NEW udp dpt:ftpnACCEPT udp -- anywhere anywhere state NEW udp dpt:domainnACCEPT udp -- anywhere anywhere state NEW udp dpt:authnACCEPT udp -- anywhere anywhere state NEW udp dpt:ntpnACCEPT icmp -- anywhere anywhere icmp echo-replynACCEPT icmp -- anywhere anywhere icmp echo-requestnACCEPT icmp -- anywhere anywhere icmp time-exceedednACCEPT icmp -- anywhere anywhere icmp destination-unreachablenLOGDROPOUT all -- anywhere anywherennChain ALLOWIN (1 references)ntarget prot opt source destinationnACCEPT all -- static.88-198-34-170.clients.your-server.de anywherenACCEPT all -- 193.42.148.113 anywheren
Как увидеть NAT правила:
По умолчанию используется фильтр таблицы. Чтобы увидеть правила NAT, введите:n
# iptables -t nat -L
Другие вариантыn
# iptables -t filter -L n# iptables -t raw -L n# iptables -t security -L n# iptables -t mangle -L n# iptables -t nat -L
Как увидеть NAT правила с номерами строк:nnИспользуйте опцию —line-numbers:n
# iptables -t nat -L --line-numbers -n
Результат:n
Chain PREROUTING (policy ACCEPT 28M packets, 1661M bytes)nnum pkts bytes target prot opt in out source destinationn1 0 0 DNAT tcp -- eth0 * 10.10.29.68 0.0.0.0/0 tcp dpt:3306 to:10.0.3.19:3306n2 0 0 DNAT tcp -- eth0 * 10.10.29.68 0.0.0.0/0 tcp dpt:11211 to:10.0.3.20:11211n3 0 0 DNAT udp -- eth0 * 10.10.29.68 0.0.0.0/0 udp dpt:11211 to:10.0.3.20:11211nnChain INPUT (policy ACCEPT 18M packets, 1030M bytes)nnum pkts bytes target prot opt in out source destinationnnChain OUTPUT (policy ACCEPT 23M packets, 1408M bytes)nnum pkts bytes target prot opt in out source destinationnnChain POSTROUTING (policy ACCEPT 33M packets, 1979M bytes)nnum pkts bytes target prot opt in out source destinationn1 38927 2336K MASQUERADE all -- * * 10.0.3.0/24 !10.0.3.0/24n2 0 0 MASQUERADE all -- * * 10.0.3.0/24 !10.0.3.0/24
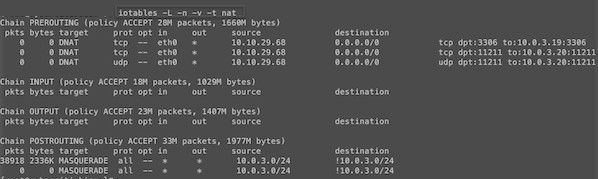
Как увидеть правила NAT со счетчиками (байтов и пакетов)nИспользуйте опцию -v для команды Iptables:n
# iptables -t nat -L -n -v
Для ip6tables
ip6tables это инструмент администрирования для пакета IPv6 фильтрации и NAT. Чтобы увидеть таблицы IPv6, введите:n
# ip6tables -L -n -v
Результат:n
Chain INPUT (policy DROP 239 packets, 16202 bytes)n pkts bytes target prot opt in out source destinationn 136K 30M ufw6-before-logging-input all * * ::/0 ::/0n 136K 30M ufw6-before-input all * * ::/0 ::/0n 241 16360 ufw6-after-input all * * ::/0 ::/0n 239 16202 ufw6-after-logging-input all * * ::/0 ::/0n 239 16202 ufw6-reject-input all * * ::/0 ::/0n 239 16202 ufw6-track-input all * * ::/0 ::/0nChain FORWARD (policy DROP 483 packets, 32628 bytes)n pkts bytes target prot opt in out source destinationn 483 32628 ufw6-before-logging-forward all * * ::/0 ::/0n 483 32628 ufw6-before-forward all * * ::/0 ::/0n 483 32628 ufw6-after-forward all * * ::/0 ::/0n 483 32628 ufw6-after-logging-forward all * * ::/0 ::/0n 483 32628 ufw6-reject-forward all * * ::/0 ::/0n 483 32628 ufw6-track-forward all * * ::/0 ::/0nChain OUTPUT (policy ACCEPT 122 packets, 8555 bytes)n pkts bytes target prot opt in out source destinationn 136K 30M ufw6-before-logging-output all * * ::/0 ::/0n 136K 30M ufw6-before-output all * * ::/0 ::/0n 183 14107 ufw6-after-output all * * ::/0 ::/0n 183 14107 ufw6-after-logging-output all * * ::/0 ::/0n 183 14107 ufw6-reject-output all * * ::/0 ::/0n 183 14107 ufw6-track-output all * * ::/0 ::/0nChain ufw6-after-forward (1 references)n pkts bytes target prot opt in out source destinationn...n....n..n pkts bytes target prot opt in out source destinationn 19 1520 ACCEPT tcp * * ::/0 ::/0 ctstate NEWn 42 4032 ACCEPT udp * * ::/0 ::/0 ctstate NEWnChain ufw6-user-forward (1 references)n pkts bytes target prot opt in out source destinationnChain ufw6-user-input (1 references)n pkts bytes target prot opt in out source destinationnChain ufw6-user-limit (0 references)n pkts bytes target prot opt in out source destinationn 0 0 LOG all * * ::/0 ::/0 limit: avg 3/min burst 5 LOG flags 0nlevel 4 prefix "[UFW LIMIT BLOCK] "n 0 0 REJECT all * * ::/0 ::/0 reject-with icmp6-port-unreachablenChain ufw6-user-limit-accept (0 references)n pkts bytes target prot opt in out source destinationn 0 0 ACCEPT all * * ::/0 ::/0nChain ufw6-user-logging-forward (0 references)n pkts bytes target prot opt in out source destinationnChain ufw6-user-logging-input (0 references)n pkts bytes target prot opt in out source destinationnChain ufw6-user-logging-output (0 references)n pkts bytes target prot opt in out source destinationnChain ufw6-user-output (1 references)n pkts bytes target prot opt in out source destination
Чтобы увидеть NAT правила и номера строк, введите:n
# ip6tables -L -n -v -t nat --line-numbers